
The ransomware sequel: alternative ways of profit harvesting
A day after we published our No Ransom Campaign decryptor in the fight against the CoinVault ransomware, we were contacted by a fellow researcher from Panda, Bart Blaze. He kindly suggested that new variants of this dreadful ransomware were available and that he would happily share them with us. After obtaining the new MD5 hashes for the files, we set out to find more clues, more files, and to analyse what these new malware variants had to reveal: three malware families that had striking similarities with each other.
In the end we found some interesting surprises (for more details about what we found, please read on).
However, the best thing was that, based on our analysis, the National High Tech Crime Unit of the Dutch police was able to apprehend two suspects last Monday.
The story begins with CoinVault
Our search began with the discovery of the first version of CoinVault, in May 2014 (please see the table at the bottom of this post for MD5s and additional information on this, and other, hashes). Interestingly enough, this sample did not run on every computer, so we have omitted any further analysis of this version here.
Then suddenly there was Comhost
Two months after we detected the initial version of CoinVault, we detected two near-identical samples. The two files differed only in how the malware was unpacked and executed from the resource section in the binary.
Both binaries loaded the same payload, an executable known as ‘comhost.exe’. Comhost was completely different from CoinVault in terms of functionality. While CoinVault fell into the category of traditional ransomware (until this point, at least), Comhost was more of an infostealer. If you cannot wait to find out more, please skip forward!
Once executed, the malware resolved the two hardcoded domain names to IP addresses. After that it started the keylogger and a timer. Once the set time had elapsed, the search for bitcoin wallets began. Most likely the attackers implemented this functionality because mining for bitcoins has become increasingly hard.
In addition, the malware was able to execute commands received from the C2.
Back to CoinVault
Fast forward two months and we saw another example of CoinVault. This time the program code had striking similarities with Comhost. For example, some functions such as fixNOIPhosts(), were almost identical, marking a clear connection between CoinVault and Comhost. The design of the program was also very similar to Comhost.
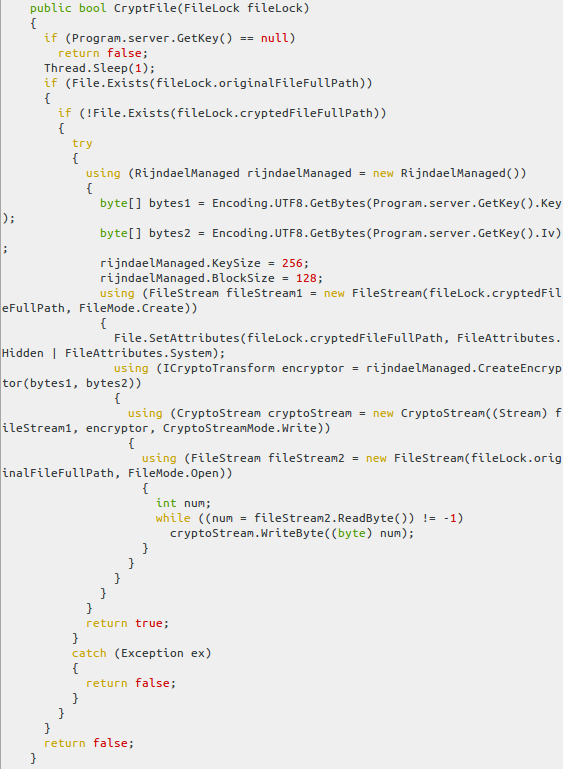
Fortunately, the authors of this piece of malware made a small mistake. Instead of overwriting the original file with encrypted content, they created a new file in the same directory with a ._clf extension.
Next, the original file was deleted by calling the File.Delete() function. Internally, this method was implemented as a call to the Win32Native.DeleteFile() function. The DeleteFile function marked the file as deleted in the MFT entry. This meant that CoinVault victims, who got infected with this specific version of the malware, were probably able to retrieve deleted files during forensic activity (when not too much disk activity had taken place after deleting the file).
The introduction of the S.H.I.E.L.D Runner and added functionality
One month after the appearance of the last CoinVault sample, a new version of Comhost was introduced. This was the first sample that contained the “S.H.I.E.L.D Runner”. The functionality of this particular piece of code has already been discussed in a previous blogpost
Apparently the malware authors were not quite satisfied with the previous version of Comhost. They forgot to add a keylogger functionality (to check for caps lock etc.) Another interesting added feature was the antivirus and default browser collection feature, which sent information on these programs to the C2. However, the most interesting new feature was the ActivecaptionWatcher class, which was able to take screenshots and send these to the C2.
Mailspreader and added obfuscation
In November 2014 we had already written about CoinVault: this post discussed the sample that appeared a few weeks after the last version of Comhost. All the samples that appeared around this date were obfuscated with Confuser. But one thing that we omitted in our analysis was a functionality that we couldn’t really place back then: the internal class ’emailDownloader’.
This class contained some interesting pieces of code that needed to be further analysed. The presence of several executable files was referenced, but where were they? And more importantly, what was their role during the infection?
As it turns out, these files were dropped by the third piece of malware from the CoinVault family: the Mailspreader. The resources section within the binary shows that several files were embedded and we extracted them in order to study them separately.
Code economy is a common pattern between all the modules found within CoinVault samples. The functionality was simple but more than enough to achieve the desired results. A thread was created and then started in order to utilize all the benefits offered by the ‘MailSpreader.exe’ file.
As mentioned before, the C2 we discovered is shared with another sample, which had similar characteristics (MD5 hash value of AF0E5A5DF0BE279AA517E2FD65CADD5C), another indicator of the relationship between CoinVault and Mailspreader.
Using these executable files and a straightforward manner of making the infection ‘invisible’, the bad guys launched a new process that was hidden almost instantly, putting all the malicious email code to work.
We still haven’t answered the question of what these executable files represent, or what their real use is in this ransomware scheme. We’ll start with ‘mailpv.exe’, which was part of CoinVault, presenting some ‘dropper’ methods to actually obtain the primary payload. For ‘nk2edit.exe’ and ‘livecv.exe.’ A quick Google search revealed their true nature: both were legitimate tools used to interact with Outlook and Windows Live messenger.
The file ‘livecv.exe‘ had an MD5 hash of D7FC749BB3B10FCC38DE498E8DB2639A, and presented a verified signature for the executable. As per the developer’s description of the utility, ‘LiveContactsView is a small utility that allows you to view the details of all contacts in your Windows Live Messenger’.
The same happened after checking ‘nk2edit.exe‘ (C1A591727E4519AC0D94C59B680E00E4). This is a convenient utility that interacts with the AutoComplete list address book in Microsoft Outlook.
RIP CoinVault
After the previous release of our CoinVault research, this threat and its creators remained silent for a while. It wasn’t until April 2015 that a new sample was spotted in the wild. The most noteworthy change was the presence of flawless Dutch phrases throughout the binary. Dutch is a relatively difficult language to write without any mistakes. Therefore, we suspected at the beginning of our research that there was a Dutch connection to the alleged malware authors.
Other interesting added functionality was the checking and killing of analysis and detection processes such as processhacker, spyhunter, roguekiller, etc. Moreover, this version also came with support for storing configuration data in .ini files.
Shortly after these new versions emerged, the Dutch police was able to seize the C2 server used by the criminals and provide us with the bitcoin wallet IDs, IVs and keys necessary for creating and providing a decryption tool.
And then…it stopped. We didn’t hear anything about CoinVault for a while and it seemed the campaign had ended.
Hello Bitcryptor
We were right that CoinVault had stopped. However, one month later BitCryptor emerged.
BitCryptor is clearly the successor of CoinVault, since most of the code is exactly the same. However, BitCryptor is not like the previous versions of CoinVault targeting a Dutch audience. All the written Dutch has been removed (as have all the links to CoinVault). A little feature has been added, that runs in the background and checks if the victim has already paid.
Conclusion
Since our initial report on CoinVault, and the presentation of the No Ransom campaign, the cybercriminals responsible for these creations have been trying to modify their creations to keep on targeting new victims. Winning the battle against ransomware is a joint effort between law enforcement, private companies and end-users. In this particular case, by working together, we achieved a great result: the apprehension of two suspects.
Nevertheless, now more than ever, education about how these threats operate and target victims is of paramount importance, along with alerting and reporting new incidents as soon as possible. Thanks to our fellow researcher Bart Blaze for sharing the samples – indeed we had a happy reversing time 🙂
MD5s:
0f1830174d7b08c0d1fcd9aea00cdc97 Trojan-Ransom.MSIL.CoinVault.l
10438b6d4f479779234ef60560d2f40c Trojan-Ransom.MSIL.CoinVault.p
174a3f6982d254a74d2db202fd87ec26 Trojan-Ransom.MSIL.CoinVault.f
289b43d3c234585285a38b2a0f4db2e3 Trojan-Ransom.MSIL.CoinVault.i
2f707ed9f368cd5838f5fb76abcd5bd9 Trojan-Ransom.MSIL.CoinVault.q
30bc17990350f44d74f4a2ca25cdb9e3 Trojan-Ransom.MSIL.CoinVault.s
45db7e51b39fd0669b4f78eedc00ad2f Trojan-Ransom.MSIL.CoinVault.n
4d46310bdfdc5c49615be5c61b13c8ae Trojan-Ransom.MSIL.CoinVault.r
4d52e7e6f4dc77c39c50ed84ce1b10b5 Trojan-Ransom.MSIL.CoinVault.s
60a5b27a525ca21026ffff1f0d0baa6a Trojan-Ransom.MSIL.CoinVault.t
648280e5ba36ff038e97e444ecdb9d8e Trojan-Ransom.MSIL.CoinVault.g
716dfea51b1a8d95859cfda38ff7fa9d Trojan-Ransom.MSIL.CoinVault.j
73848ec02d5d9f4d0fdd5be31ef86449 Trojan-Ransom.MSIL.CoinVault.u
78fd303be07db8fa35b98645bef10ca4 Trojan-Ransom.MSIL.CoinVault.v
7fff4eabcdfb21e7884a240e668f1e8b Trojan-Ransom.MSIL.CoinVault.i
80db8e54a1a28e0167a4d66b3be84a5d Trojan-Ransom.MSIL.CoinVault.af
876050d738f434fc149970cc0d073dbe Trojan-Ransom.MSIL.CoinVault.w
8e1bdc1c484bc03880c67424d80e351d Trojan-Ransom.MSIL.CoinVault.x
a6499dac9a7b59830c77442eb030c93c Trojan-Ransom.MSIL.CoinVault.a
a76df48770a6cffc62e4d1a21749071b Trojan-Ransom.MSIL.CoinVault.m
a90d5d05728fec4c592393c7f4ec173e Trojan-Ransom.MSIL.CoinVault.e
ac4b5ce347820c8817afd49eacee3ec5 Trojan-Ransom.MSIL.CoinVault.y
af0e5a5df0be279aa517e2fd65cadd5c Trojan-Ransom.MSIL.CoinVault.z
aff8fefe76cc51d5e7120ef3f422ce29 Trojan-Ransom.MSIL.CoinVault.ah
b3a7fc445abfba3429094542049063c2 Trojan-Ransom.MSIL.CoinVault.x
b3bb6facbb557ddd9aada93f6b2efab8 Trojan-Ransom.MSIL.CoinVault.h
b3e1c2fce9763a2bdd08223c406bcf7f Trojan-Ransom.MSIL.CoinVault.aa
b92ec8ccc085b853545fc54781d0c1a3 Trojan-Ransom.MSIL.CoinVault.ab
be1f48b6b4c0515ac0d865713968e1c3 Trojan-Ransom.MSIL.CoinVault.ac
cb91d0db64d9245426c7789ed00ba4d3 Trojan-Ransom.MSIL.CoinVault.k
d5f291f2bc38873e145f6e6b13fb05db Trojan-Ransom.MSIL.CoinVault.d
d7732b4132440e9e8902080032897c15 Trojan-Ransom.MSIL.CoinVault.ad
d92e1be4fdfdea99dfa23de27f3bb568 Trojan-Ransom.MSIL.CoinVault.ae
e6227eaefc147e66e3c7fa87a7e90fd6 Trojan-Ransom.MSIL.CoinVault.af
e7414d82d69b902b5bc1efd0f3e201d7 Trojan-Ransom.MSIL.CoinVault.b
e883706376bb45ef53ec52fbd090a29a Trojan-Ransom.MSIL.CoinVault.ai
e8b83233071fd752e29b436113d5ea9d Trojan-Ransom.MSIL.CoinVault.ag
f293970741bbe0ee0c1b8ce6cb045d4d Trojan-Ransom.MSIL.CoinVault.b





























Coinvault, are we reaching the end of the nightmare?