
Our colleagues already delved into how cybercriminals attack companies through compromised email addresses of employees, and how to protect against such attacks using SPF, DKIM and DMARC technologies. But despite the obvious pluses of these solutions, there is a way to bypass them that we want to discuss.
But let’s start from a different angle: how relevant is email these days? After all, this year saw a sharp rise in the popularity of video-conferencing tools, preceded by several years of healthy growth in the use of instant messengers, in particular, WhatsApp and Telegram. Nevertheless, email is still the main means of online communication, at least in the business world. Indirect confirmation of this is the increase in the number and quality of Business Email Compromise (BEC) attacks. According to data from the US Internet Crime Complaint Center (IC3), the financial damage from such attacks has risen sevenfold in the past five years.
Financial damage from BEC attacks, 2015–2019 (download)
Data for 2020 has not yet been published, but given the COVID-19 pandemic and the mass shift of employees to remote working, it is safe to assume that the number of BEC attacks will only grow. Initial threat landscape studies also point to this.
Lookalike domains in BEC
A feature of BEC is the emphasis not on the technical side (cybercriminals’ options are rather limited when it comes to email), but on social engineering. Typically, attacks of this kind combine technical and social techniques to achieve greater efficiency. The three protection technologies mentioned above cope with most combinations well enough. But there is one exception: lookalike-domain attacks. The method is simple in essence: the cybercriminals register a domain that looks very similar to that of the target company or a partner firm. Messages sent from this domain sail through Sender Policy Framework (SPF) authentication, possess a DomainKeys Identified Mail (DKIM) cryptographic signature, and generally do not arouse the suspicions of security systems. The snag is that these emails are phishing. And if written believably enough — with a corporate template, stressing the urgency of the matter, etc. — they will likely fool the victim.
Here are some examples of fake domain names:
| Original domain | Fake domain |
| netflix.com | netffix.com |
| kaspersky.com | kapersky.com |
| uralairlines.ru | uralairilnes.ru |
As you can see, the fake differs from the original by only one letter added (or removed) so that a closer look is required to spot it.
For an overview of the use of fake domains, we compiled statistics on lookalike spoofing for Q3 2020. Having analyzed the data, we concluded that this year’s pandemic has significantly changed the direction of cybercriminal activity. Whereas before, the focus of such attacks was the financial sector, now the service sector is in the firing line, including various e-commerce services: food delivery, online shopping, buying air tickets, etc. Domains related to this sector accounted for 34.7% of the total number of attacks in Q3.
Distribution of detected lookalike domains by category, Q3 2020 (download)
Also note the rise in the IT sector’s share in 2020: up from 17.9% in Q1 to 22.2% in Q3. This is to be expected, since the mass transition to remote working was bound to impact the overall situation.
A word about lookalikes
Unlike spam mailings, which tend to be large in both scale and duration, attacks involving lookalike domains, like any BEC attack, target a specific victim (or group of victims). Consequently, emails are few and well thought out, and the domains are extremely short lived. We see that half of all fake domains are used only once, and in 73% of cases the domain is only active for just one day. This renders traditional signature-based anti-spam solutions (detect an attack, create a rule) effectively useless, thus the need arises for proactive protection. There are two common and at the same time simple methods available to companies keen to guard at least in some measure against lookalike and other such attacks.
The first is for the company itself to register domains with typos, and set up redirects to its official domain. This reduces cybercriminals’ ability to register a plausible fake, but does not nullify it completely or prevent counterfeiting of domains belonging to partners, contractors and other organizations which the company deals with.
The second is to compile lists of plausible fake names for both the company’s domain and those of partners and contractors. Next, the list is loaded into the anti-spam solution, which preemptively blocks all messages arriving from the fakes. The main drawback of this method is the same as before: it is impossible to cover all possible fake domains, especially if the company works with many counterparties. Plus, there is the ever-present human factor — one typo in the list of tens or hundreds of domain names can lead to a security breach or the filtering out of emails from a legitimate domain instead of a fake one, causing additional headaches for business units.
When simple solutions no longer suited our clients, they came to us for something more complex. The result was a method that requires no user interaction. In a nutshell, it automatically compiles a global list of legitimate domains that could potentially be faked, on which basis it analyzes and blocks messages from lookalike domains. In essence, it is proactive.
How it works
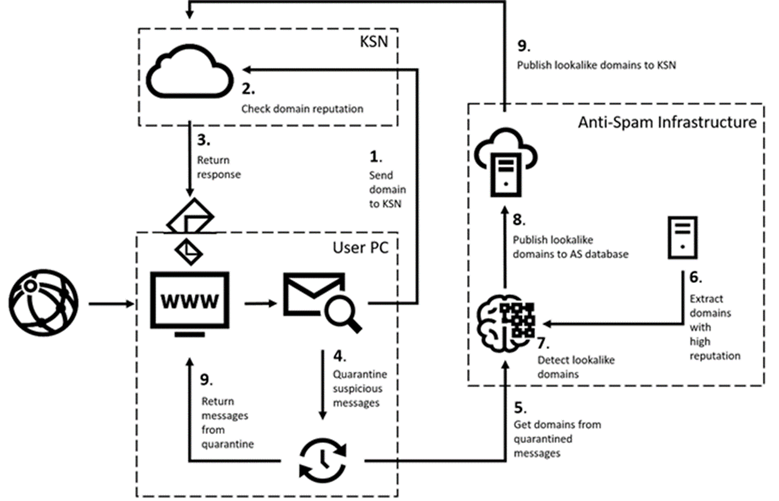
Protection against lookalike-domain attacks is three-pronged: client-side processing; domain reputation check in Kaspersky Security Network; infrastructure-side processing. The general principle is shown schematically below:
In practice, it goes as follows. On receiving an email, the technology forwards the sender domain to Kaspersky Security Network (KSN), which matches it against the list of lookalike domains already known to us. If the sender domain is found, the message is instantly blocked (steps 1 to 3). If there is no information about it, the email is quarantined for a short fixed period (step 4). This gives time for the technology to check the domain according to the set algorithm, and, if it recognizes it as fake, to add it to the list of lookalike domains in KSN. After the email leaves quarantine, it is rescanned (step 9) and blocked, since by then the list of lookalike domains has been updated.
Let’s take a look at how sender verification works and how the list of lookalike domains gets updated. Information about quarantined messages is sent to the KSN database together with additional metadata, including the sender domain (step 5). At the first stage of analysis, the domain undergoes a “suspiciousness” check based on a wide range of criteria, such as Whois data, DNS records, certificates, and so on; the purpose of this stage is to quickly sift out domains that are clearly legitimate, but not yet known to our system. Henceforth, emails from these domains are no longer quarantined, because KSN now has information about them. At the second stage, the system compares the similarity of suspicious domains and addresses in our global list of legitimate domains (step 7), which includes the domains of our clients and their counterparties. This list is generated automatically based on an assessment of the frequency with which legitimate messages are sent from the domain and the uniformity of the mail flow over time. The extent to which the overall picture matches the behavior of employees in terms of business correspondence determines the reputation of the domain (step 6). If the resemblance of the scammer’s domain to a legitimate address is high, the sender domain too is added to the list of lookalike domains and all messages sent from it are blocked.
Our approach is more complex than simply registering lookalike domains to the company and enables real-time blocking of attacks that use such domains as soon as they appear. In addition, the human factor is eliminated, and the global list of legitimate domains stays current thanks to automatic updates.















Lookalike domains and how to outfox them