
Attacchi di phishing nei confronti dei clienti di Poste Italiane
The number of serious cyber-attacks detected over the last two years has increased so much that new attacks rarely cause much surprise. It’s now commonplace for antivirus companies to issue a report about the discovery of another botnet or highly sophisticated malware campaign that is gathering data.
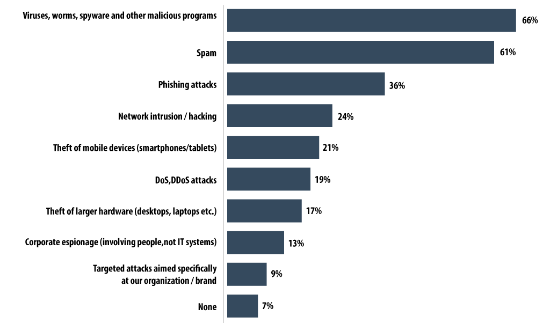
Companies are increasingly falling victim to cyber-attacks. According to a survey conducted by Kaspersky Lab and B2B International, 91% of the organizations polled suffered a cyber-attack at least once over a 12-month period, while 9% were the victims of targeted attacks.
The extensive use of computers and other digital devices in all areas of business has created ideal conditions for cyber espionage programs and malware capable of stealing corporate data. The potential is so great that malicious programs may soon completely replace company insiders as a way of gathering information. However, the risks to the corporate sector do not end there. This dependence on the reliable operation of computers and the channels that connect them means cybercriminals are presented with a variety of other ways to target companies using destructive programs, from so-called encryptors and shredders that spread like the plague in a corporate environment, to an army of zombies that devours every available resource on web servers and data transfer networks.
The motives
- Stealing information. The theft of valuable corporate data, commercial secrets, personal data of staff and customers, and monitoring of company activities are common goals of businesses that turn to cybercriminals to penetrate their competitors’ networks or government intelligence agencies.
- Wiping data or blocking infrastructure operations. Some malicious programs are used to carry out a form of sabotage – destroying critical data or disrupting a company’s operational infrastructure. For example, the Wiper and Shamoon Trojans irrevocably wipe system data from workstations and servers.
- Stealing money. Companies can incur financial losses as a result of activity by specialized Trojan programs capable of stealing money via online banking systems or which perform targeted attacks on the internal resources of processing centers.
- Damaging a company’s reputation. Malicious users are attracted by successful companies and official websites with high visitor numbers, especially those in the Internet service sphere. A compromised corporate site that redirects visitors to malicious resources, malicious advertising banners or banners that display a political message can cause significant damage to a company’s reputation in the eyes of its clients.
Another serious reputational risk is linked to the theft of digital certificates. For public certification authorities, for example, the loss of certificates or the penetration of the digital certificate infrastructure can, in some cases, lead to a complete breakdown in trust and the subsequent closure of the business. - Financial losses. One popular method of causing direct damage to a company or organization is by subjecting it to a DDoS attack. Cybercriminals are continuously coming up with new ways of carrying out such attacks. As a result of a DDoS attack a company’s public-facing web resources can be put out of action for several days. In situations like this clients not only have no access to a company’s services – resulting in direct financial losses for the latter – but they also start looking for a more reliable company, which in turn reduces the customer base and results in long-term financial losses. 2013 saw an increase in the popularity of DNS Amplification attacks where malicious users, with the help of botnets, send recursive queries to DNS servers, reflecting the amplified response to the targeted system. This was the tactic used in one of the most powerful DDoS attacks this year – theattack on the Spamhaus site.
Target organizations
When it comes to the mass distribution of malicious programs any company can be affected. Notorious banking Trojans such as ZeuS and SpyEye can penetrate the computers of even small commercial organizations resulting in the loss of money and intellectual property.
However, there are also numerous cases of carefully planned activity aimed at infecting the network infrastructure of a specific organization or individual. The results of our research showed that in 2013 the victims of these targeted attacks included companies from the oil and telecommunications industries, scientific research centers, as well as companies working in sectors such as aerospace, shipbuilding and other hi-tech industries.
Preparing an attack
Cybercriminals have a large array of sophisticated tools to help them penetrate corporate networks. Planning a targeted attack on a company can take several months, after which all available tactics are deployed, starting with social engineering and progressing to exploits for unknown software vulnerabilities.
The attackers meticulously examine the target company’s commercial profile, public resources, websites, employee profiles on social networks, announcements and the results of various presentations, exhibitions etc. for any piece of useful information. When planning a strategy for an intrusion and subsequent data theft, the criminals may study the company’s network infrastructure, network resources and communication centers.
When planning their attack, the cybercriminals may create a fake malicious website that is an exact copy of the target’s own site and register it with a similar domain name. It will then be used to trick users and infect their computers.
Intrusion techniques
One of the most popular techniques for inserting malware in corporate networks in 2013 was to send emails containing malicious attachments to company employees. More often than not, the documents in these emails were in familiar Word, Excel or PDF formats. When the attached file is opened a software vulnerability – if present – is exploited and the system is infected by a malicious program.
Weak link
Employees who regularly have to communicate with people outside their corporate structure are often the recipients of malicious emails. More often than not the recipients work in the public relations department.
Departments involved in hiring new staff also receive lots of emails from external users. A cybercriminal may pretend to be a potential candidate for a job, and send a resume in an infected PDF file. Of course, the file will be opened by an HR employee, and if there is a vulnerability on the workstation, it will then be infected.
Finance departments may also receive malicious messages under the guise of requests or demands from the tax authorities, while legal departments might receive messages that appear to be from judicial bodies, the police or other government agencies.
Social Engineering
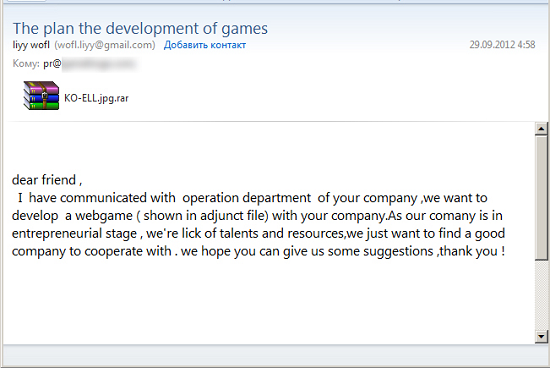
The content of the message is intended to pique the interest of the employee it addresses, whether in relation to his/her job responsibilities or the company’s general sphere of business. For instance, the hacking group Winnti sent messages to private video game manufacturers suggesting possible cooperation as part of a targeted attack:
The spyware Miniduke was distributed in a letter about Ukraine’s foreign policy plans and Ukraine-NATO relations:
Vulnerabilities and exploits
Cybercriminals actively use exploits to known software vulnerabilities.
The renowned Red October, for instance, used at least three different exploits to known vulnerabilities in Microsoft Office: CVE-2009-3129 (MS Excel), CVE-2010-3333 (MS Word) and CVE-2012-0158 (MS Word). Nettraveler used an exploit of CVE-2013-2465, which is a vulnerability of Java versions 5, 6 and 7; it was only patched by Oracle in June 2013.
However, so-called zero-day vulnerabilities – currently unknown to the software manufacturer – are the most dangerous. Cybercriminals actively search popular programs for unknown loopholes and create exploits to them. If such a vulnerability exists in a piece of software, it is very likely to get exploited.Miniduke used such a vulnerability (CVE-2013-0640) in Adobe Reader versions 9, 10, 11 – it was unknown at the time of the attack.
Technologies
Cybercriminals continuously improve malware, using unconventional approaches and solutions to steal information.
Red October, once it got a foothold within a system, worked as a multifunctional module-based platform. It added various modules to the infected system depending on the set target. Each of these modules performed a certain range of actions: from collecting information about the infected computer and its network infrastructure, stealing various passwords, keylogging, self-propagation, sending stolen information etc.
It should be also noted that cybercriminals have also responded to the development of mobile technologies and the spread of mobile devices in corporate environments. A modern smartphone or tablet PC is effectively a full-bodied workstation storing a huge amount of data, and thus is a potential target for cybercriminals. The creators of Red October developed dedicated modules which determined when smartphones running under Apple iOS, Windows Mobile as well as cellphones manufactured by Nokia connected to the infected workstation, copied data from them and sent it to the C&C server.
The creators of Kimsuky have integrated an entire module into their piece of malware which can remotely manage infected systems. Interestingly, they have done so with the help of TeamViewer, a quite legitimate remote management tool, by introducing slight modifications into its program code. After that, operators could manual connect to infected computers to collect and copy information that was of interest.
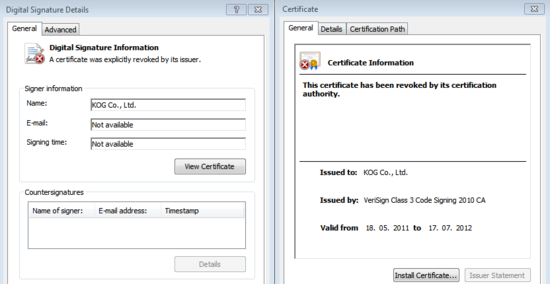
The Winnti hacker group stole digital certificates from the corporate networks of online game manufacturers, and used them to sign their malicious driver, subsequently infecting other companies. For example, a digital certificate was stolen from the South Korean company KOG. When we informed the company about the theft, the compromised certificate was revoked.
This is the revoked certificate:
In addition, the 64-bit Trojan included a fully functional backdoor module. This is the first case, as far as we know, when a 64-bit malicious program has been used with a valid digital signature belonging to a legitimate company.
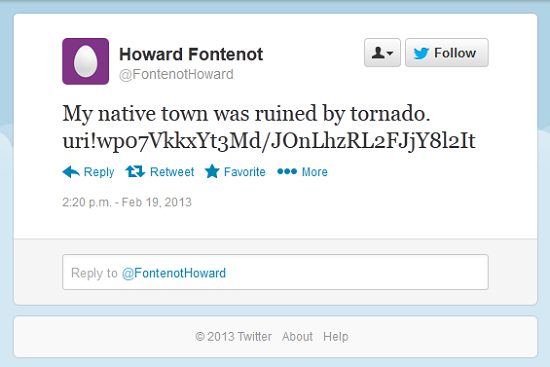
The Miniduke spyware used Twitter to receive information from C&C servers. Miniduke’s operators used dedicated accounts to publish specially crafted tweets which included an encoded C&C URL address.
The Trojan read Twitter on an infected computer and used the address to connect to the C&C.
What gets stolen
Cybercriminals are interested in stealing information of all kinds. It could be cutting-edge technology developed by companies and research institutes, source codes of software products, financial and legal documents, personal information about employees and clients, and any other information that may constitute a commercial secret. This information is often stored in plain text in corporate networks in the form of electronic documents, draft documents, reports, drawings, presentations, images etc.
As stated above, cybercriminals take different approaches to data gathering. Some malicious programs collect practically all types of electronic documents. For example, Red October was interested in documents in txt, csv, eml, doc, vsd, sxw, odt, docx, rtf, pdf, mdb, xls, wab, rst, xps, iau, etc. formats; the malicious program sent all of these to the C&C servers.
Another approach, which we identified with Kimsuky and Icefog is essentially a manual analysis of the data stored in corporate networks using remote-access technologies integrated into malware on infected workstations, and the subsequent copying of those documents that were specifically required or of value to the cybercriminals. When launching such attacks, cybercriminals take into account all the details of the targeted company and have a clear understanding of what data formats are used in that company and what types of information are stored. Thus, during Kimsuky and Icefog attacks, the targeted companies lost documents which were very specific to their activities and were stored in the HWP format which is widely used in South Korea.
The rise of the cybermercenaries
While analyzing the latest targeted attacks, we came to the conclusion that a new category of attackers has emerged. We call them cybermercenaries. These are organized groups of highly qualified hackers who can be hired by governments or private companies to organize and conduct complex, effective targeted attacks aimed at stealing information and destroying data or infrastructure.
Cybermercenaries are given a contract which stipulates the goals and a description of the task, after which they start to thoroughly prepare for and then launch the attack. While earlier attacks tended to steal information indiscriminately, cybermercenaries now aim to lay their hands on very specific documents or the contacts of people who might own the target information.
In 2013, we investigated the activity of the cybermercenary group Icefog, which launched target attacks under the same name. During the investigation, we managed to locate an Icefog operator activity log, which detailed all the attack activities. It became obvious from that log that the criminals not only have a good knowledge of Chinese, Korean and Japanese, but also know exactly where to look for the information they are interested in.
Consequences of high-profile disclosures
2013 saw some major disclosures about attacks launched by spyware that were related, directly or indirectly, to the activities of various governments. These disclosures could potentially lead to a loss of confidence in global services and corporations and greater interest in creating national equivalents of global services. This might lead to a peculiar type of de-globalization, causing a growing demand for IT in general, but a fragmentation of the users of the global network and a certain segmentation of online services. Already in many countries, there are local versions of global services, including national search engines, mail services, national IM services and even local social networks.
This growing number of new national software products and services is delivered by national manufacturers. These companies are typically smaller in size and budget than global market leaders. As a result it’s possible that their products may not be of the same quality as those of the larger international companies. Our experience of investigating cyber-attacks suggests that the smaller and less experienced the software developer is, the more vulnerabilities will be found in its code. As a result targeted attacks become easier and more effective.
Moreover, as states seize the initiative in controlling information and hardware resources, some states may legally oblige local companies to use national software products or online services, which may ultimately affect the security of the corporate sector as well.




















Kaspersky Security Bulletin 2013. Corporate threats