
We have become aware of unusual malware that was found in some banks in Singapore. This malware has many names – it is known as Adwind RAT (Remote Access Tool), AlienSpy, Frutas, Unrecom, Sockrat, JSocket, and jRat. It is a backdoor available for purchase, and is written entirely in Java which makes it cross-platform. According to the author, the backdoor component (called the server) can run on Windows, Mac OS, Linux and Android platforms providing rich capabilities for remote control, data gathering, data exfiltration and lateral movement.
While it is mostly used by opportunistic attackers and distributed in massive spam campaigns there are indications that some of the Adwind samples were used in targeted attacks. In August 2015 AlienSpy popped up in the news related to cyber-espionage against an Argentinian prosecutor who was found dead in January 2015.
#Adwind RAT is an unusual #Java backdoor that was found in some banks in #Singapore #TheSAS2016
Tweet
The malware sample we received was sent by email to some banks in Singapore on behalf of a major Malaysian bank. The IP address of the e-mail senders points to a server in Romania while the mail server and account used belong to a company located in Russia.
Adwind is a backdoor written purely in Java that targets system supporting the Java runtime environment. The malware program operates by sending out system information and accepting commands from a remote attacker. These commands can be used, among other things, to display messages on the system, open URLs, update the malware, download/execute files, and download/load plugins. A significant amount of additional functionality can be provided through downloadable plugins, including such things as remote control options and shell command execution.
We would like to encourage enterprises to review the purpose of using a Java platform and to disable it for all unauthorized sources.
What exactly is Adwind?
Adwind is a cross-platform, multifunctional backdoor, which can run on Windows, Mac OS, Linux and Android OS.
Is this a nation-state sponsored campaign?
This is not a nation-state sponsored campaign. We believe that it was developed and used mostly by cybercriminals.
Who are the victims? / What can you say about the targets of the attacks?
The victims range from random people that launched the malware following an opportunistic attack to specific organizations, most of which are small and medium-sized businesses.
How did you become aware of this threat? Who reported it?
From one of our partners we received part of an email with a .JAR attachment. The profile of the partner company and the contents of the email indicated a targeted attack attempt. While the partner was not compromised we decided to check the attachment, which led us to the malware platform.
How does Adwind infect computers?
Adwind doesn’t self-infect computers or spread automatically. It relies on user interaction: double-clicking the .JAR attachment in the email or doing the same from an archive. Alternatively, it can be spread via other containers like .hta or .vbs files, which install Java if it’s not available on the system and download the main Adwind.JAR file from a remote server.
Are the attackers using any zero-day vulnerabilities?
We have not seen attackers using zero-day vulnerabilities together with Adwind.
What exactly is being stolen from the target machines?
Limited only by the intelligence needs of the attackers, the malware can:
- collect keystrokes
- steal cached passwords and grab data from web forms
- take screenshots
- take pictures and record video from the webcam
- record sound from the microphone
- transfer files
- collect general system and user information
- steal keys for cryptocurrency wallets
- manage SMS (for Android)
- steals VPN certificates
Is this a Windows-only threat? Which versions of Windows are targeted? Are there Mac OS X or Linux variants?
This malware is capable of running on any platform that has a modern Java runtime environment installed, which includes all Java-supported versions of Windows, Mac OS X, Linux and potentially other platforms which run Java.
Have you seen any evidence of a mobile component – iOS, Android or BlackBerry?
We have seen Adwind .apk files that can run on Android OS, however iOS and BlackBerry are out of the scope of this platform.
It seems Adwind is all about Java. Why do you think it is so?
Java applications by design should be platform independent. While certain system architectures are quite specific and there is a set of Java libraries designed for them, general purpose code may run on any system that has a Java runtime environment installed. This makes Java a very convenient platform for which to develop malware that can run on any platform.
Do you know the total number of victims?
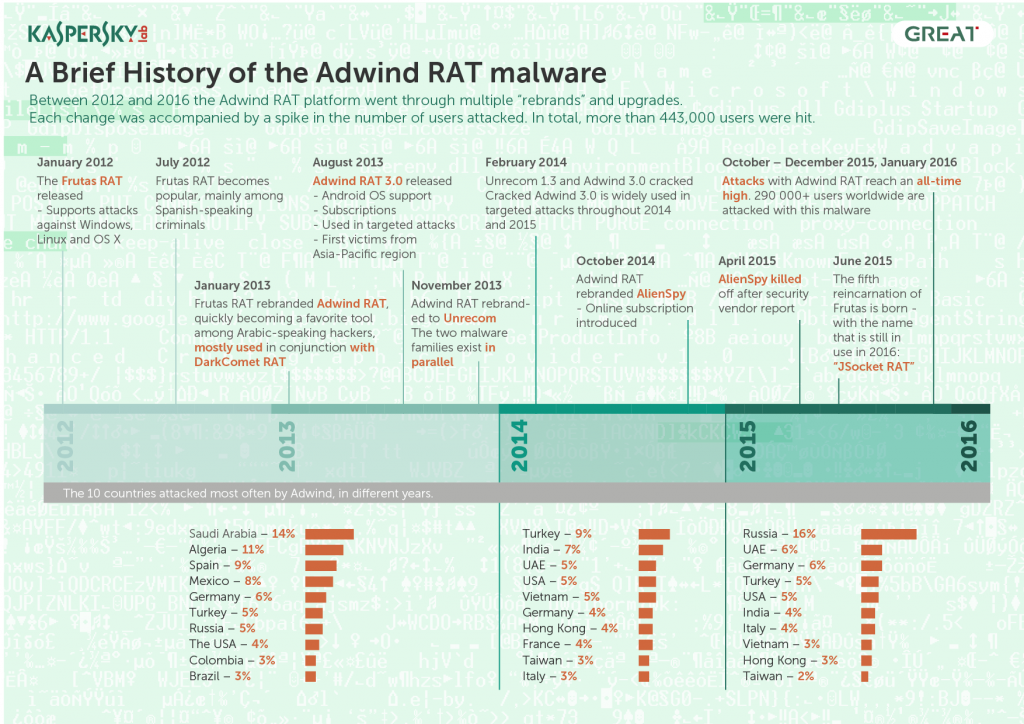
We have our own estimate of targets attacked by this malware. It is more than 443,000 covering the period from 2013 to the beginning of 2016.
What is the geography of victims?
The geography of victims changed over time. In 2013, Arabic and Spanish-speaking countries were the top targets. In 2014, the most attacked countries were Turkey and India, followed by UAE, the US and Vietnam. In 2015, Russia was the most attacked country, with UAE and Turkey again near the top, along with the USA, Turkey and Germany.
What are the attacked industries?
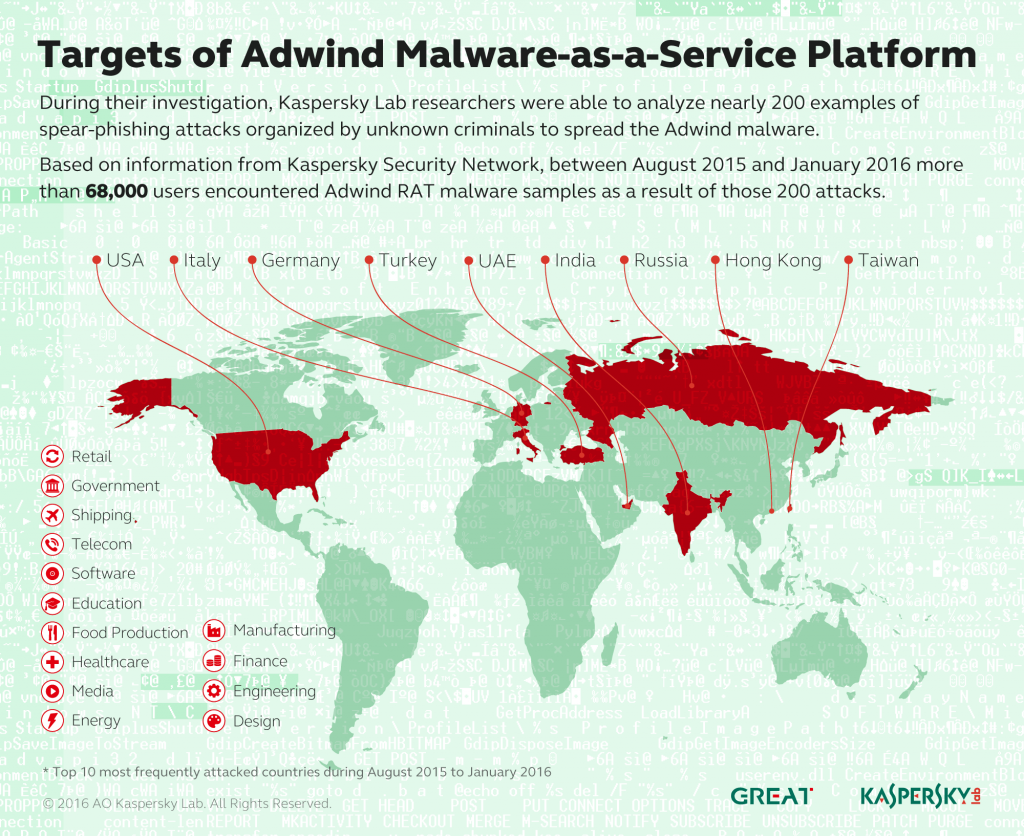
During their investigation the Kaspersky Lab researchers were able to analyze nearly 200 examples of spear-phishing attacks organized by unknown criminals to spread the Adwind malware, and were able to identify the industries most of the targets worked in:
- Manufacturing
- Finance
- Engineering
- Design
- Retail
- Government
- Shipping
- Telecom
- Software
- Education
- Food production
- Healthcare
- Media
- Energy
Based on information from Kaspersky Security Network, the 200 examples of spear-phishing attacks observed in the six months between August 2015 and January 2016 resulted in Adwind RAT malware samples being encountered by more than 68,000 users.
Who are the clients of Adwind? Where are they from? How many? Are they APT actors?
To begin with, Adwind only had a Spanish interface; however it now also has an English interface and is recognized by cybercriminals from many countries. We believe that clients of the Adwind platform fall into the following categories:
- Scammers that want to move to the next level (using malware for more advanced fraud)
- Unfair competitors
- Cyber-mercenaries (spies for hire)
- Private individuals that want to spy on people they know
How is this different from any other APT attack?
Adwind is not an APT attack. It is a platform with rich capabilities that cybercriminals can use to conduct cyber-espionage.
Are there multiple variants of Adwind? Are there any major differences in the variants?
There have been multiple generations of Adwind, which has been continuously developed and supported since at least 2012. The differences are mostly about malware features and available modules, however all variants rely on the same basic scheme of client-server communication. It’s designed to send commands in an ad-hoc manner, which introduces a constraint of controlling a large number of compromised machines. We believe that it’s not suitable for even medium-sized botnets and used only for targeted network penetrations.
Is the command-and-control servers used by Adwind still active? Have you been able to sinkhole any of the C&Cs?
The Adwind malware is used by hundreds of criminals, which means that there are hundreds of command and control servers. Some of them are down, some are up, the others are turned on as required. It’s not easy and not efficient to take them down in the traditional way. Most of them rely on free Dynamic DNS providers and are not real domain registrations.
Who is responsible for this threat?
We cannot speculate publically about attribution.
How long have the attackers been active?
The users of Adwind malware have been active since at least 2012 with a large spike of users at the end of 2015.
Did the attackers use any interesting/advanced technologies?
Generally speaking, the Java platform is not a common platform for malware at all. It is mainly related to the requirement of having a Java runtime environment on the victim’s system, the size of the generated code and availability of decompilers for Java classes. The author of the Adwind malware attempted to solve all these problems by introducing a number of workarounds.
Does Kaspersky Lab detect all variants of this malware?
Kaspersky Lab products detect all variants of this malware that we know about. The full list is available in the Appendix of our public report.
Are there Indicators of Compromise (IOCs) to help victims identify the intrusion?
Yes, there are many known domains and IP addresses used by the Adwind attackers. The full list is available in the Appendix of our public report.
What is JSocket? How long does it exist?
JSocket is the latest reincarnation of Adwind RAT, and available through online subscription. It was launched in June 2015 and is still running.
What is the problem with just interrupting the JSocket service?
Interrupting the service by suspending the domain or taking down the server wasn’t efficient in the past and led to yet another rebranding and restart of the platform.
What is the difference between JSocket and Adwind?
The Adwind RAT and the JSocket RAT are based on the same source code and were most likely developed by the same author. While Adwind was abandoned some time ago, JSocket still exists and is just another “brand” of the same RAT. As JSocket is the latest variant of the backdoor it has many more features and a rebuilt UI.
How many people you think are behind the whole MaaS platform?
We believe that the platform is in the hands of just one hardworking individual, who sometimes outsources tasks to external developers.
You estimated the revenue of the whole service as 200k per year. How did you calculate this figure?
Based on users’ activity on the internal message board and some other observations, we estimated a number of users in the system as 1,800 by the end of 2015. By making certain assumptions on the percentage of paid accounts, service costs and most probable distribution of the paid customers, we concluded that such a service may generate up to $200K USD annually. However, this is just an estimation of revenue, which doesn’t necessarily mean that the author has already received this money. One important fact is that the latest version of the portal was launched only in summer 2015.
Have you reported your findings to LEA? What was the outcome?
We believe that reporting to Law Enforcement is the best way to combat cybercrime. Yes, we have reported the case of the attempted computer attack which we investigated in depth from the very beginning, based on information provided by our research partner. The information was received but apparently it takes time to verify and process such reports to start an investigation. The reporter doesn’t normally get an update from a police investigation, with the exception of requests for some additional information.
To find out more about withstanding Adwind-based attacks, read this article in the Kaspersky Business Blog.
For any inquiries, please contact intelreports@kaspersky.com
Adwind: FAQ




















Karen Rodriguez
I am a current victim of this attack and can have vital information for your research. Please contact me.
Cavite Lemis
Thanks, site was taken off.
amin
could you mentioned the name of other country is infected?
Karen Rodriguez
The USA and mainly Silicon Valley, CA.
Dennis Guadalupe
I am current víctima of this attack also… I live in BCS, Mexico. Can you help or benefit from analyzing infected MACBook Pro_
c kolo
I think I have a ZERO-DAY use being used with some sort of RAT that is using old certificates.
Robert Davidson
I know my phone and tablet are infected with this Rat. My case is very unique and law enforcement is not helping. And I live in a small community and anyone who works on computers will not touch my issue. Because what has happened to me, long story. But I believe I know someone involved in this and they work for Cisco and L3 Communications here in Texas. I’m asking for someone to please help me. Call 903 335 3959, if you email me they will intercept it. Need help seriously.
Noah Spada
Practical blog post ! I was fascinated by the information ! Does someone know where I might be able to get a template FLCS Check Register Template document to type on ?
Nouran
Could you please give an example of an attack on an infrastructure in the energy sector