
Being a malware researcher means you are always busy with the struggle against mountains of malware and cyberattacks around the world. Over the past decade, the number of daily new malware findings raised up to unimaginable heights: with hundreds of thousands of malware samples per day! However, while there are some rare and dangerous malware, not every sample is as malicious as these. Moreover, some of the biggest threats exist only when several ingredients are put together, including multiple malware tools, malicious infrastructure, and interactive commands coming from their operators.
This is why, instead of only looking at malware, we have started tracking groups of attackers and have focused on campaigns and isolated incidents. This has been an increasingly challenging job, because it involves searching for a needle in a haystack of haystacks, and sometimes we’re searching across very distant locations. There are different ways of undergoing searches like this, but the most reliable is that used by law enforcement agencies: full digital forensics. This procedure is time consuming, highly dependent on the availability of a skilled expert on site, and usually involves physical travelling. Our natural response to this problem is to find a solution – and surprisingly no one was offering one. Well, at least not one that was up to our standards!
My Bitscout project started years ago as a hobby. I had been playing with the creation and customisation of LiveCDs. Some time afterwards, when we needed to find traces of a certain attacker on a compromised PC in an African country, I thought I could help. I built a simple and minimal LiveCD on Linux, with a preconfigured VPN client and SSH server, and shared it with the system owner over the Internet. The owner burnt the CD and started the infected PC from it. It worked like a charm: a full control over remote computer connected via the Internet became available from my desk. It was a slow connection but it luckily for me I didn’t use a bandwidth-heavy remote desktop access. A text terminal was more than enough to do the job over a slow modem line. I managed to help the owner acquire a forensically sound disk image of the compromised system, point out the malware and related file locations and, most importantly, extract precious pieces of information, including a malware dropper and spearphishing email.
Time passed, and similar requests appeared again and again. We worked with INTERPOL using the same model: a law enforcement officer would go to the physical disk acquisition location, and with permission from local law enforcement agencies, would let us find the most important evidence on the site – instantly. This cut our time traveling and helped law enforcement with the quick discovery of key artefacts left after a cyberattack.
Some time afterwards many new scenarios started popping up:
- Manually remediatiating an infected PC (from a rootkit)
- Sharing remote sessions let us educate new users and increase the speed of analysis
- Once, I traveled to a customer but I had no expensive enterprise SAS disk controller with me to complete a disk image acquisition with. Using LiveCD I was able to clone the disk via the original server hardware. And I didn’t even have to stay in the cold server room to monitor the progress!
We also worked on making the tool simple and friendly for users who are not familiar with commandline Linux environments. Still, for the sake of having a small disk size, we decided to keep away from GUI tools and X11 servers. Naturally we settled on a TUI (Text UI), which is simple to operate with just arrow keys.
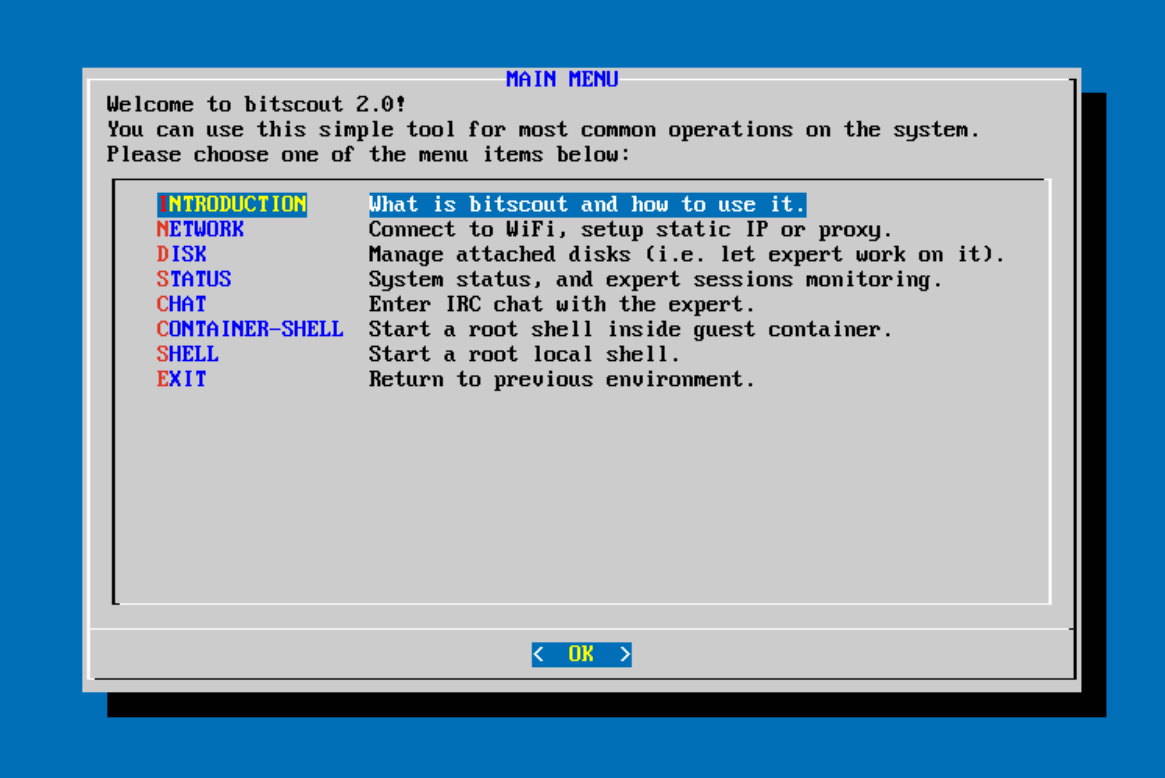 Bitscout 2.0 main window for general users
Bitscout 2.0 main window for general users
However, when you work with someone who has never met you, trust is an inherent problem. Just think about it: would you let some remote expert have access to your precious system? If so, I’d be delighted to work with you. But if I were in your shoes, I would be paranoid, and would like to control the process myself. This is quite natural and is something that bothered me in the previous versions of LiveCDs.
This issue of trust could be resolved if we could somehow limit an expert’s access to hardware, and monitor and record everything that he/she does. Following this idea, we built a new version of Bitscout: Bitscout 2.0, which we have just released. The remote expert has root privileges only inside a virtual unprivileged container. The expert can access only those disk devices that are permitted by the owner, and it’s possible for them to install additional software and change system files – all without the risk of compromising the host system or data on the harddrive. This is all done in RAM, and is gone once the system is shutdown. In addition, all remote sessions are recorded and stored outside of the container. This provides a good level of isolation and a way to reconstruct the forensic process for learning purposes, or prove the existince of evidence.
But that’s not all! Bitscout 2.0 is not only based on open-source tools, it is actually an open source tool itself that let’s you build your own LiveCDs – your own types of Bitscout systems. So, the tool is essentially a collection of scripts which anyone can validate, customize and improve.
And you are welcome to do so, because now it’s on Github: https://github.com/vitaly-kamluk/bitscout
Bitscout – The Free Remote Digital Forensics Tool Builder




















Dennis Karlsson
Amazing projekt.
Were can i find more info on that.
Im very interesting in the produkt.
But i want to Learn more.
I work as a forensiker in sweden
ADOLFO
Hi,
After executing ./automake,sh command I receive the following message :
Problem executing scripts APT::Update::Post-Invoke-Success ‘if /usr/bin/test -w /var/cache/app-info -a -e /usr/bin/appstreamcli; then appstreamcli refresh > /dev/null; fi’
I´m using Ubuntu 16.0.4 LTS desktop installed on a VMware Workstation 12 pro.
Regards,
Adolfo Cáceres